Planning and Managing group-based identities and lifecycle can be very complex in an Azure AD environment due to the different types of groups available and the various group sources available in a tenant that is connected to on-premises identity infrastructure or even Exchange Online. Understanding the use cases for each group type and where its attributes and membership can be managed can be complex. Microsoft has published the “Compare groups” article which partially addresses this topic, but not with the level of detail that is required for those planning out the group identity management structure for a Microsoft 365 adoption. The information provided below is intended to fill that gap.
Group Sources and Types in a Microsoft 365 / Azure AD Tenant
Native Azure AD Group Types
First, groups in Azure AD can originate directly in Azure AD. Just two types of groups can originate directly in Azure AD:
Security (native Azure AD)
Microsoft 365
Other Azure AD Group Types
Additionally, Azure AD groups can originate outside of Azure AD by being synchronized into Azure AD from a connected source such as Exchange Online or from one or more on-premises Active Directory environments (which may also include Exchange on-premises organizations and attributes). Presently, many if not most enterprise organizations that have a Microsoft 365 / Azure Ad Tenant have configured on-premises identities to synchronize with Azure AD via Azure AD Connect or another identity management solution. Depending on the configuration of that identity synchronization solution, various on-premises group types will be synchronized to Azure AD (and connected Microsoft 365 services). Similarly, groups originating in Exchange Online can appear in Azure AD. Specifically, the group types that originate from these other sources, but which can appear in Azure AD include the following types:
Security (synced from AD)
Mail enabled Security (from AD/Exchange or Exchange Online)
Distribution (from AD/Exchange or Exchange Online)
Group Characteristics and Capabilities by Type and Source
Group Types Listing
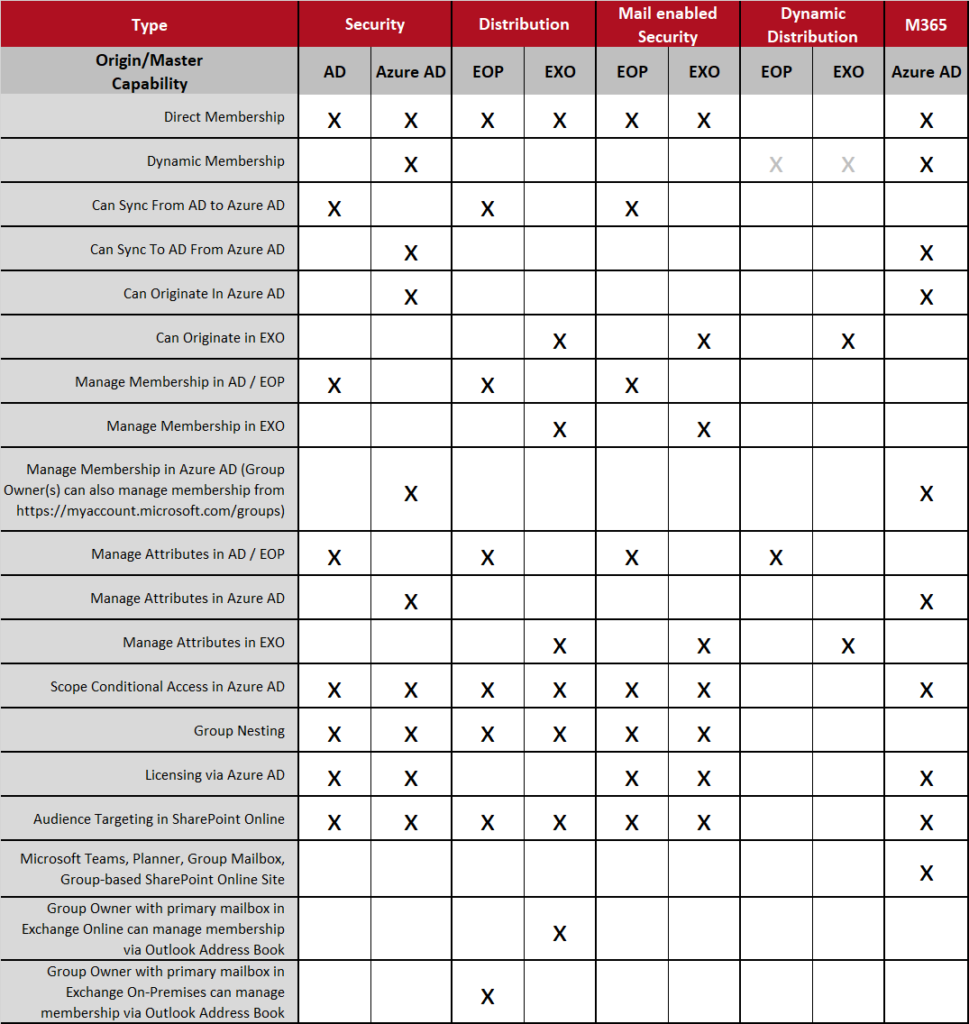
The following table describes the available characteristics and capabilities of a group based on its type and source (Origin/Master). The Group Types included are as follows:
Security (regardless of source, Azure AD or AD): can be used as a security principal in various access control lists for permissions to folders, labels, policies, sites, applications, etc. Many other potential uses.
Microsoft 365 (source is always Azure AD): can be used like a Security group (as a security principal) but also is the source of membership for Microsoft Teams, Planners, Group Mailboxes, Group based SharePoint Online sites, and other Microsoft 365 services.
Distribution (source is always Exchange On-Premises /AD or Exchange Online): can be used for email distribution and some other applications like audience targeting in SharePoint Online.
Dynamic Distribution (source is always Exchange On-Premises or Exchange Online): can be used for mail distribution. Does not sync from the source environment to Azure AD – never appears in Azure AD.
Mail-Enabled Security (: same as security plus email distribution. Not considered a best practice to use in most cases (usually better to separate email distribution from security group applications).
Group Sources (Origin/Master) Listing
The following table describes the available characteristics and capabilities of a group based on its type and source (Origin/Master). The Group Sources included are as follows:
AD: An Active Directory Forest (one or more domains) hosted outside Azure AD (usually on-premises but could be in hosted in a cloud environment).
Azure AD: The directory service associated with a Microsoft Azure / Microsoft 365 Tenant
EOP: Exchange On-Premises. An Exchange organization connected to an Active Directory environment.
EXO: Exchange Online. An Exchange Online organization connected to the Exchange Online environment and connected to an Azure AD / Microsoft 365 Tenant
TypeSecurityDistributionMail enabled SecurityDynamic DistributionM365
Origin/Master
CapabilityADAzure ADEOPEXOEOPEXOEOPEXOAzure AD
Direct Membershipxxxxxxx
Dynamic Membershipxxxx
Can Sync From AD to Azure ADxxx
Can Sync To AD From Azure ADxx
Can Originate In Azure ADxx
Can Originate in EXOxxx
Manage Membership in AD / EOPxxx
Manage Membership in EXOxx
Manage Membership in Azure AD (Group Owner(s) can also manage membership from https://myaccount.microsoft.com/groups)xx
Manage Attributes in AD / EOPxxxx
Manage Attributes in Azure ADxx
Manage Attributes in EXOxxx
Scope Conditional Access in Azure ADxxxxxxx
Group Nestingxxxxxx
Licensing via Azure ADxxxxx
Audience Targeting in SharePoint Onlinexxxxxxx
Microsoft Teams, Planner, Group Mailbox, Group-based SharePoint Online Sitex
Group Owner with primary mailbox in Exchange Online can manage membership via Outlook Address Bookx
Group Owner with primary mailbox in Exchange On-Premises can manage membership via Outlook Address Bookx




Leave A Comment